𝐖𝐡𝐲 𝐔𝐬𝐞𝐫 𝐁𝐮𝐟𝐟𝐞𝐫𝐬 𝐀𝐫𝐞 𝐔𝐧𝐬𝐮𝐢𝐭𝐚𝐛𝐥𝐞 𝐟𝐨𝐫 𝐊𝐞𝐫𝐧𝐞𝐥 𝐨𝐫 𝐃𝐌𝐀 𝐔𝐬𝐞 𝐛𝐲 𝐃𝐞𝐟𝐚𝐮𝐥𝐭
Why User Buffers Need Extra Care to Work with Kernel and DMA
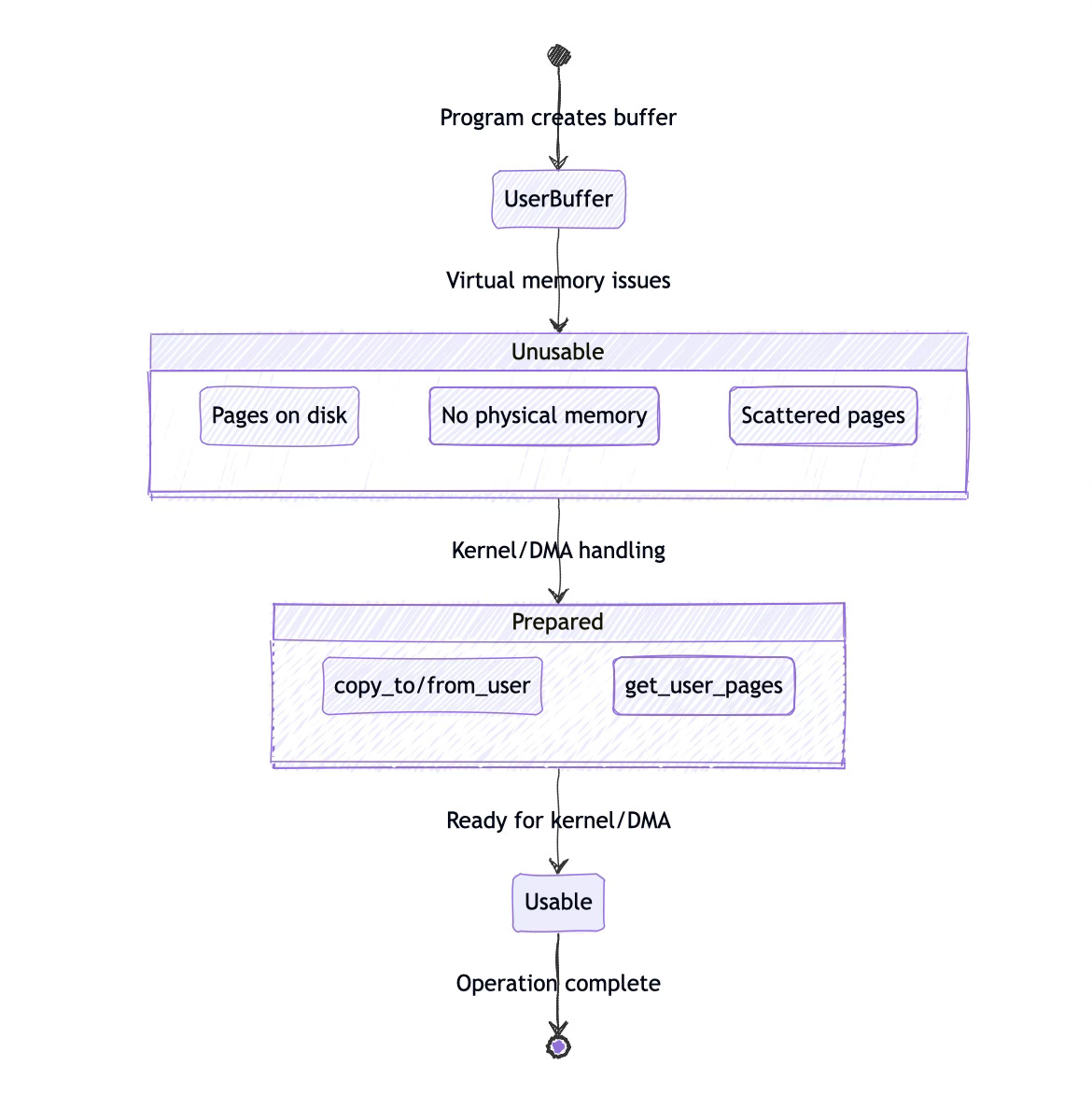
Let's talk about why user-space virtual addresses, or user buffers, aren't something the kernel or DMA can just grab and use without some extra work. It comes down to how virtual memory works in user processes.
When a program runs, its virtual addresses don't always map directly to physical memory. Those pages might be swapped out to disk to free up RAM for other tasks. If the kernel or a DMA operation tried to access a user buffer that's been swapped out, it'd hit a wall. The system would either stall waiting for the page to be swapped back in or just fail outright. That's a mess nobody wants.
Then there's the issue of allocation. User-space virtual addresses might not even point to real, allocated memory. Think about a program that hasn't initialized a buffer or one that's been unmapped. The virtual address could be valid in the process's address space but not tied to any physical page.
The kernel can't just assume a user buffer is ready to go; it'd need to check, and that checking adds overhead. DMA is even pickier since it needs physical memory that's locked down and contiguous, something user buffers don't guarantee.
𝘞𝘩𝘺 𝘥𝘰𝘦𝘴 𝘵𝘩𝘪𝘴 𝘮𝘢𝘵𝘵𝘦𝘳 𝘧𝘰𝘳 𝘵𝘩𝘦 𝘬𝘦𝘳𝘯𝘦𝘭 𝘴𝘱𝘦𝘤𝘪𝘧𝘪𝘤𝘢𝘭𝘭𝘺? The kernel runs in a privileged mode with direct access to physical memory or its own mapped address space. It needs reliable, predictable access to data. User buffers, tied to a process's virtual memory, are subject to all sorts of user-space shenanigans like page faults or memory protection.
The kernel could handle those, but it’s not built to babysit user-space memory by default. That’s why you’ll see mechanisms like 𝐜𝐨𝐩𝐲_𝐭𝐨_𝐮𝐬𝐞𝐫 or 𝐜𝐨𝐩𝐲_𝐟𝐫𝐨𝐦_𝐮𝐬𝐞𝐫 to safely move data between user and kernel space.
DMA throws in another wrinkle. Hardware devices doing DMA don't understand virtual memory. They need physical addresses, and those addresses better point to memory that's pinned in RAM, not something that might vanish mid-transfer.
User buffers, being virtual and potentially scattered across non-contiguous pages, are a poor fit unless the kernel does some heavy lifting first, like pinning pages with 𝐠𝐞𝐭_𝐮𝐬𝐞𝐫_𝐩𝐚𝐠𝐞𝐬 or mapping them properly.
So, 𝐮𝐬𝐞𝐫 𝐛𝐮𝐟𝐟𝐞𝐫𝐬 aren't inherently bad; they just need preparation to play nice with the kernel or 𝐃𝐌𝐀. The kernel can copy data to its own buffers, pin user pages, or map them into a usable form, but none of that happens automatically.
That’s why, out of the box, user buffers are a no-go for these low-level operations. It's all about ensuring the system stays stable and efficient.