How SSH Multiplexing Reuses Master Connections for Efficient Sessions
The hidden SSH optimisation that turns multiple terminal connections into shared channels over a single TCP socket—and why it matters for every developer.
Table of Contents
Introduction
SSH Connection Architecture: The Foundation
The Master Connection: Your Persistent Highway
Control Sockets: The Coordination Layer
Channels: Multiple Streams in One Connection
Configuring SSH Multiplexing
The Multiplexing Sequence: Step by Step
What Happens When Terminals Close?
Port Forwarding and Multiplexing
Low-Level Mechanics: Under the Hood
Performance Benefits and Trade-offs
Common Challenges and Solutions
Debugging and Monitoring
Integration with Session Management
Advanced Configuration Patterns
Security Considerations
Summary: Why Multiplexing Matters
References and Further Reading
Introduction
SSH has been the backbone of remote server administration for decades, but there's an elegant optimization hiding in plain sight that many developers and system administrators never fully explore. When you open multiple terminal windows and connect to the same server, you might wonder: does each ssh command create a brand new TCP connection, or is there something smarter happening under the hood?
The answer lies in SSH multiplexing—a feature that allows multiple SSH sessions to piggyback on a single TCP connection. Instead of establishing a new connection for each terminal, multiplexing reuses an existing "master" connection, dramatically reducing connection overhead and improving performance. This isn't just theoretical; it's the difference between waiting several seconds for each new connection versus near-instantaneous session establishment.
Understanding how this works requires peeling back the layers of SSH's architecture to see how master connections, control sockets, and channels orchestrate this efficiency. We'll explore the mechanics that make this possible and why it matters for anyone managing remote systems regularly.
SSH Connection Architecture: The Foundation
Before diving into multiplexing, let's establish how SSH normally handles connections. When you run ssh user@server, several things happen in sequence:
TCP Handshake: Your client establishes a TCP connection to port 22 (or whatever port the server uses)
SSH Protocol Negotiation: Client and server agree on encryption algorithms, host key verification
Authentication: Password, public key, or other authentication methods
Channel Establishment: A channel is opened for your interactive shell session
Each of these steps takes time and resources. The TCP handshake alone requires at least one round-trip to the server. Authentication can involve multiple round-trips, especially with public key authentication where the server might need to verify signatures.
Think of a traditional SSH connection like making a phone call—each conversation requires dialing, waiting for pickup, and establishing who you are before you can start talking. SSH multiplexing is more like a conference call system where you dial once, and then additional participants can join the same call without going through the entire setup process again.
The Master Connection: Your Persistent Highway
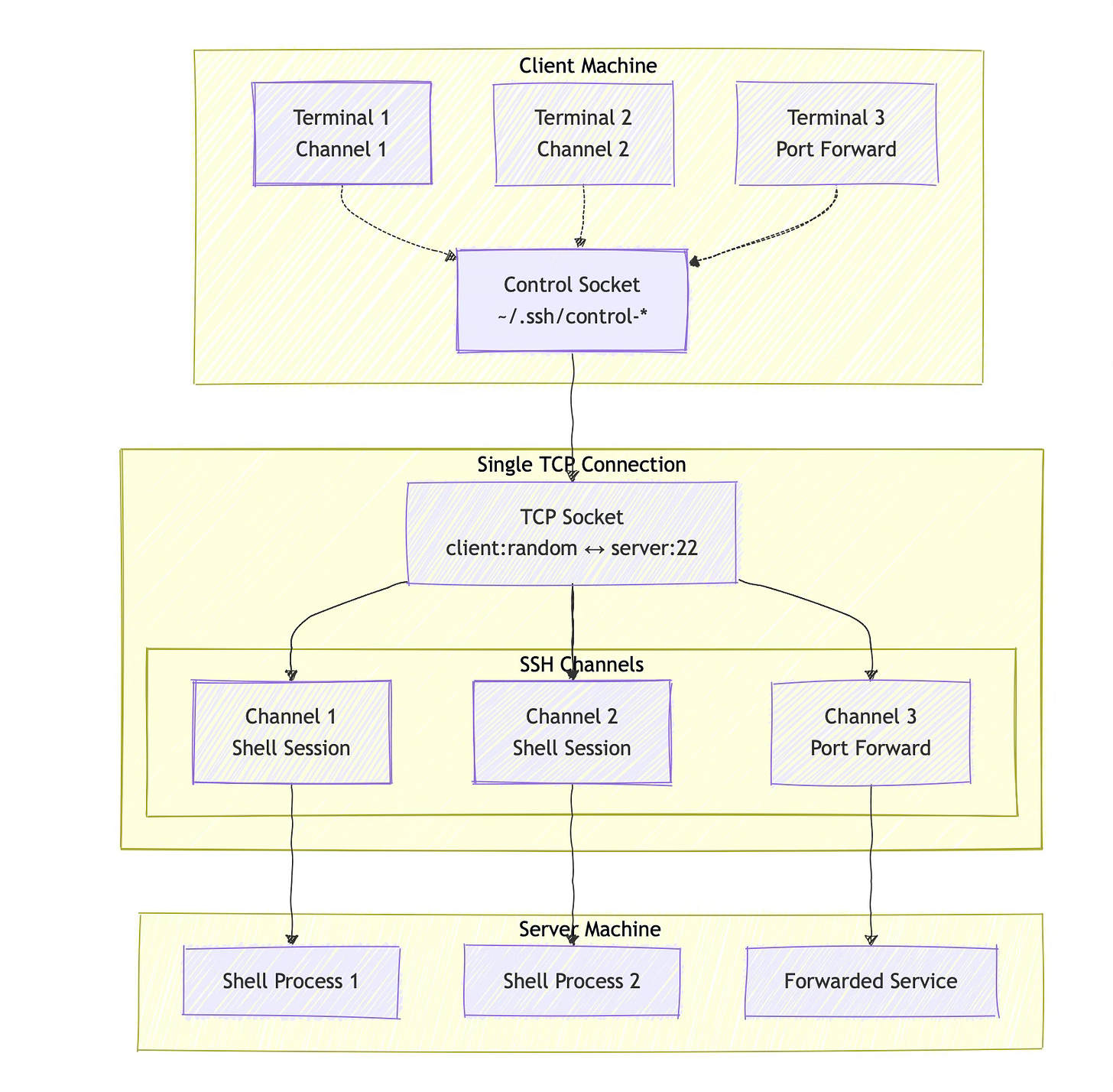
The master connection is the foundation of SSH multiplexing. It's the initial TCP connection established by the first SSH session, but with a crucial difference: it's designed to stick around and serve multiple sessions simultaneously.
When you configure SSH multiplexing (we'll cover the configuration shortly), the first ssh command to a server doesn't just establish a connection for itself—it becomes the "master" that other sessions can attach to. This master connection handles all the heavy lifting: maintaining the encrypted tunnel, managing authentication state, and coordinating multiple data streams.
The master connection persists even after individual sessions close. You might exit your first terminal window, but if other sessions are still active—or if you've configured persistence—the underlying TCP connection remains open, ready for new sessions to attach.
Control Sockets: The Coordination Layer
Here's where SSH multiplexing gets clever. The master connection needs a way to communicate with new SSH processes on your local machine. Enter the control socket—a Unix domain socket that acts as a coordination point between SSH processes.
Here: Terminal 2 never establishes its own TCP connection. Instead, it leverages the existing master connection established by Terminal 1, simply adding a new channel to carry its session data.
When the master connection starts, it creates a control socket file (typically in ~/.ssh/ with a name like control-user@hostname:port). This file isn't just a marker; it's an active communication channel. When you run ssh in a new terminal, the SSH client first checks for an existing control socket. If it finds one, it connects to the socket and essentially says, "I need a new session to this server."
The master process, listening on the control socket, responds by opening a new channel within the existing TCP connection. No new TCP handshake, no re-authentication—just a new logical stream within the established connection.
I remember struggling with control socket permissions the first time I set this up. The socket file must be readable and writable only by your user (permissions 600), otherwise SSH refuses to use it for security reasons. It's one of those details that can trip you up if you're not careful about file permissions.
Channels: Multiple Streams in One Connection
SSH channels are the secret sauce that makes multiplexing possible. The SSH protocol was designed from the beginning to support multiple channels within a single connection. Each channel is a separate logical stream that can carry different types of data: interactive shell sessions, port forwards, file transfers, or remote command execution.
When you establish the master connection and open your first terminal session, that session gets its own channel—let's call it Channel 1. When you open a second terminal and connect via the existing master connection, SSH allocates Channel 2 for that session. Both channels share the same underlying TCP connection, but they're completely independent from the application perspective.
This channel architecture is what allows SSH multiplexing to be transparent to the applications using it. Your shell doesn't know or care that it's sharing a TCP connection with other sessions. As far as it's concerned, it has its own dedicated connection to the server.
The SSH protocol supports dozens of simultaneous channels per connection, though practical limits depend on server configuration and resource constraints. Most servers can comfortably handle 10-20 simultaneous channels per connection without issues.
Configuring SSH Multiplexing
Setting up multiplexing requires adding a few lines to your SSH configuration. Here's a typical setup in ~/.ssh/config:
Host myserver
HostName server.example.com
User myusername
ControlMaster auto
ControlPath ~/.ssh/control-%r@%h:%p
ControlPersist 10mLet's break down each directive:
ControlMaster auto: Enables multiplexing with intelligent behavior. The first connection becomes the master automatically
ControlPath: Specifies where to create the control socket. The
%r@%h:%ppattern expands touser@hostname:port, ensuring unique sockets for different destinationsControlPersist 10m: Keeps the master connection alive for 10 minutes after the last session closes
The auto setting for ControlMaster is particularly elegant. It means you don't need separate configuration for master and slave connections—SSH figures out automatically whether to create a new master or attach to an existing one.
The Multiplexing Sequence: Step by Step
Let's walk through what happens when you use multiplexing in practice:
Terminal 1 - Establishing the Master:
You run
ssh myserverSSH checks for an existing control socket at
~/.ssh/control-myusername@server.example.com:22No socket exists, so SSH initiates a full connection: TCP handshake, protocol negotiation, authentication
SSH creates the control socket and marks this connection as the master
A channel is opened for your interactive shell session
You get your shell prompt
Terminal 2 - Reusing the Master:
You open a new terminal and run
ssh myserverSSH finds the existing control socket
Instead of creating a new TCP connection, SSH connects to the control socket
The master process receives the request and opens a new channel in the existing TCP connection
You get a shell prompt almost instantly
The speed difference is dramatic. The first connection might take 2-3 seconds (especially over high-latency connections), while subsequent connections happen in milliseconds.
What Happens When Terminals Close?
This is where ControlPersist becomes important. When you close Terminal 1 (the one that established the master), the master connection doesn't immediately die. Instead, it transitions into a background state, continuing to serve other active sessions.
If you close all terminals connected to the server, the master connection still persists for the configured duration (10 minutes in our example). During this time, new SSH connections will still reuse the master, avoiding the connection overhead entirely.
After the persistence timeout expires, the master connection closes, and the control socket is cleaned up. The next SSH connection will need to establish a new master.
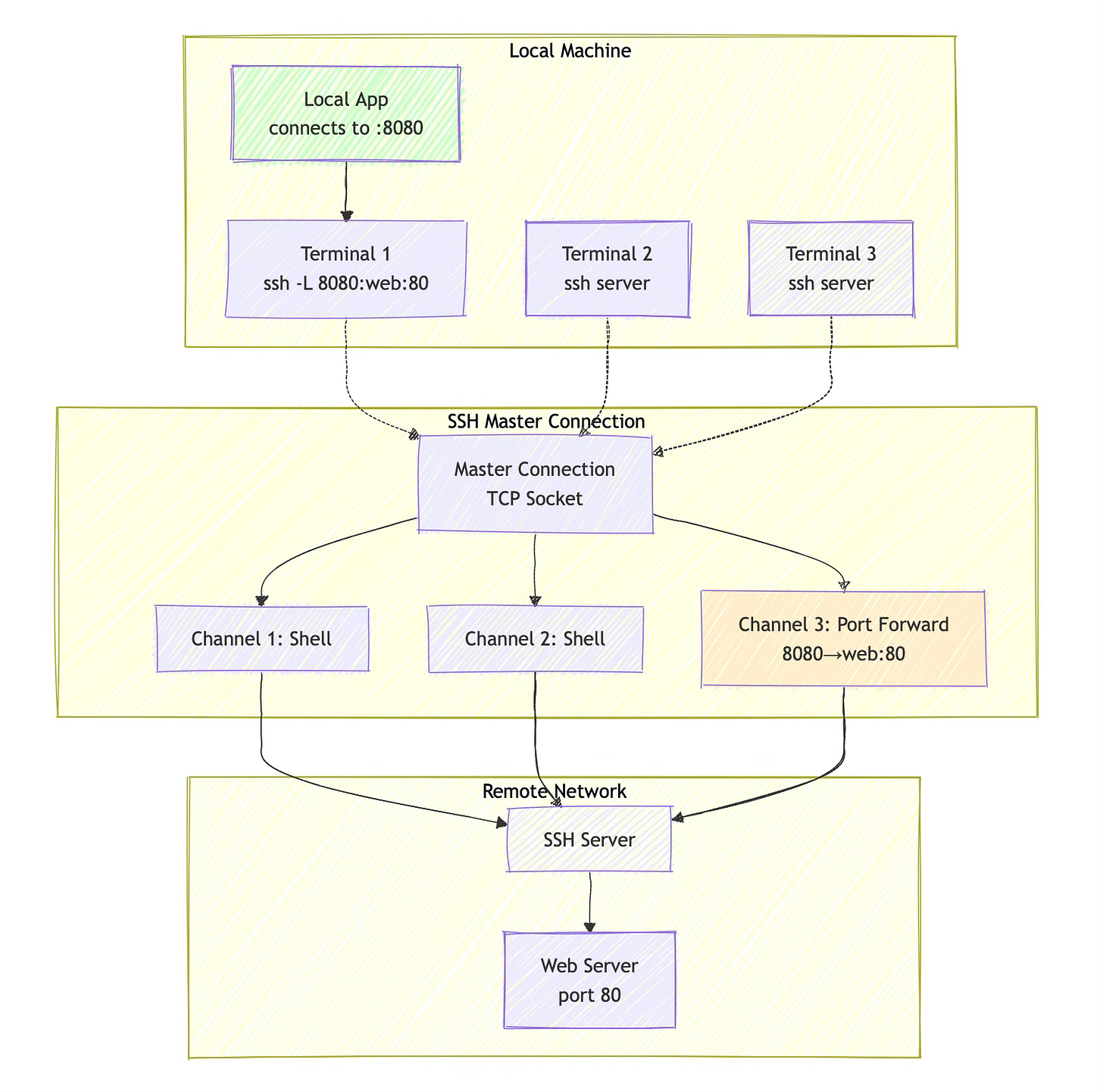
Port Forwarding and Multiplexing
SSH multiplexing becomes even more powerful when you consider port forwarding.
When you establish a port forward with the master connection:
ssh -L 8080:localhost:80 myserverThat forwarded port becomes available to all sessions using the master connection. You don't need to specify the port forward again in subsequent terminals—it's already there, managed by the master connection.
However, there's a gotcha: if you try to establish a conflicting port forward in a multiplexed session, SSH will typically reject it. The master connection owns the port forwarding configuration, and individual sessions can't modify it.
Low-Level Mechanics: Under the Hood
For those curious about the implementation details, SSH multiplexing relies on some interesting low-level mechanisms. The control socket is implemented as a Unix domain socket, which provides fast inter-process communication on the same machine.
When a new SSH process wants to multiplex, it performs roughly these steps:
Socket Connection: Connect to the Unix domain socket specified by ControlPath
Request Transmission: Send a multiplexing request containing session parameters
Channel Allocation: The master process allocates a new channel ID and establishes the channel
File Descriptor Passing: The master passes file descriptors for stdin/stdout/stderr back to the client process
Here's a simplified example of how you might interact with a control socket programmatically in C:
#include <sys/socket.h>
#include <sys/un.h>
int connect_control_socket(const char* socket_path) {
int sock = socket(AF_UNIX, SOCK_STREAM, 0);
if (sock < 0) return -1;
struct sockaddr_un addr;
memset(&addr, 0, sizeof(addr));
addr.sun_family = AF_UNIX;
strncpy(addr.sun_path, socket_path, sizeof(addr.sun_path) - 1);
if (connect(sock, (struct sockaddr*)&addr, sizeof(addr)) < 0) {
close(sock);
return -1;
}
return sock;
}This is obviously simplified—the real SSH implementation handles protocol negotiation, error handling, and security checks—but it illustrates the basic mechanism.
Performance Benefits and Trade-offs
The performance benefits of SSH multiplexing are substantial:
Reduced Latency: New sessions establish in milliseconds instead of seconds
Lower Resource Usage: Both client and server use fewer TCP connections and associated resources
Reduced Authentication Overhead: No need to re-authenticate for each session
Network Efficiency: Less connection churn reduces network congestion
However, there are some trade-offs to consider:
Single Point of Failure: If the master connection dies, all multiplexed sessions die with it
Resource Concentration: All sessions share the bandwidth and processing of a single TCP connection
Complexity: Debugging connection issues becomes more complex when multiple sessions are involved
In practice, the benefits far outweigh the drawbacks for most use cases. The single point of failure concern is mitigated by SSH's robust reconnection mechanisms and the fact that you can always establish a new master connection if needed.
Common Challenges and Solutions
Control Socket Permissions The most common issue is incorrect permissions on the control socket. SSH is strict about security—the socket file must be owned by you and readable/writable only by you:
chmod 600 ~/.ssh/control-*Stale Control Sockets Sometimes control sockets become stale (pointing to a dead master process). SSH usually detects this automatically, but you can manually clean up if needed:
rm ~/.ssh/control-*Server-Side Limits Some SSH servers limit the number of channels per connection. If you hit these limits, you'll see errors like "channel open failed." The solution is usually to increase the server's MaxSessions directive in sshd_config.
Port Forwarding Conflicts When using port forwarding with multiplexing, remember that the master connection owns the forwards. You can't establish conflicting forwards in multiplexed sessions. Plan your port forwards when establishing the master, or use SSH's dynamic port forwarding (-D) for more flexibility.
Debugging and Monitoring
To verify that multiplexing is working, use SSH's verbose mode:
ssh -v myserverLook for lines like:
debug1: multiplexing control connection
debug1: master_connect_sock: path /home/user/.ssh/control-user@server:22You can also monitor TCP connections to verify you're not creating multiple connections:
ss -tn | grep :22With multiplexing working correctly, you should see only one TCP connection to your server's port 22, regardless of how many SSH sessions you have open.
Integration with Session Management
SSH multiplexing pairs beautifully with terminal multiplexers like tmux or screen. Here's a powerful combination:
Use SSH multiplexing to reduce connection overhead
Use tmux on the remote server to create persistent, reattachable sessions
Use ControlPersist to keep the SSH master connection alive
This setup gives you both connection efficiency and session persistence. You can close your laptop, come back hours later, and quickly reattach to your remote tmux sessions via the persisted SSH master connection.
Advanced Configuration Patterns
For more sophisticated setups, you can use different ControlPersist values for different hosts:
Host production-*
ControlMaster auto
ControlPath ~/.ssh/control-%r@%h:%p
ControlPersist 30m
Host development-*
ControlMaster auto
ControlPath ~/.ssh/control-%r@%h:%p
ControlPersist 5mThis keeps production connections alive longer (since they're likely to be reused), while allowing development connections to timeout more quickly.
Security Considerations
SSH multiplexing doesn't significantly change the security model—the master connection uses the same encryption and authentication as a regular SSH connection. However, there are a few considerations:
Control Socket Security: The control socket file is a potential attack vector. SSH mitigates this with strict permission checking, but keep your home directory secure
Session Isolation: All multiplexed sessions share the master connection's security context. If one session is compromised, it potentially affects others
Persistence Risk: ControlPersist keeps authenticated connections open longer, potentially expanding the window for exploitation if your local machine is compromised
These risks are generally acceptable for most use cases, especially when weighed against the security benefits of reduced authentication frequency and connection reuse.
Summary: Why Multiplexing Matters
SSH multiplexing transforms the experience of working with remote servers. What starts as a simple optimization—reusing TCP connections—cascades into significant improvements in workflow efficiency, resource usage, and user experience.
The key concepts to remember:
Master Connection: The first SSH session establishes a persistent TCP connection that others can reuse
Control Socket: A local file that coordinates between SSH processes and the master connection
Channels: Independent logical streams within the shared TCP connection
Persistence: Connections can outlive individual sessions, enabling rapid reconnection
For system administrators and developers who regularly work with remote servers, multiplexing isn't just a nice-to-have—it's a fundamental efficiency improvement that compounds over time. The few minutes spent configuring it properly pays dividends in reduced waiting time and improved productivity.
References and Further Reading
OpenSSH Manual Pages:
man ssh_config,man sshRFC 4254: The Secure Shell (SSH) Connection Protocol - Covers the SSH channel architecture
TCP/IP Illustrated, Volume 1 - For deeper understanding of TCP connection mechanics
Advanced SSH configurations in production environments often build on these multiplexing concepts
SSH multiplexing represents the kind of thoughtful optimization that makes powerful tools even more powerful. By understanding how master connections, control sockets, and channels work together, you're better equipped to leverage SSH's full potential in your daily work with remote systems.